An interesting conversation came up last week in my LinkedIn feed. It went something like “why do defenders use a framework like MITRE ATT&CK when attackers don’t?” The reality of this is that cyber criminals are lazy and only when the easy thing doesn’t work will they find more inventive ways to breach our defenses.
The idea reminded me of some basic analysis that I did on the MITRE ATT&CK framework awhile ago. Specifically, they have releases a set of STIX scripts against their TAXII server to make the underlying data model open to analysis. Now if that didn’t make sense, no worries, let’s walk through the results. However, if that is as exciting to you as it was to me, check out their GitHub page.
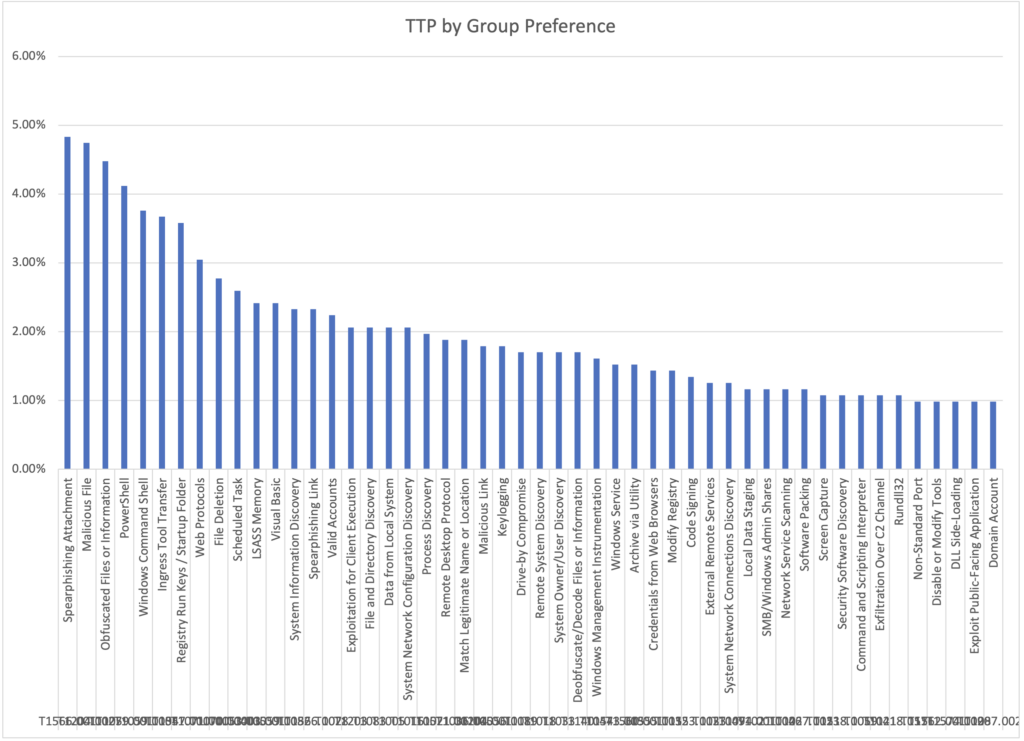
My first question was, what are the most preferred techniques. The top 10 were:
- Spearfishing Attachment
- Malicious File
- Obfuscated Files or Information
- PowerShell
- Windows Command Shell
- Ingress Tool Transfer
- Registry Run Keys / Startup Folder
- Web Protocols
- File Deletion
- Scheduled Tasks
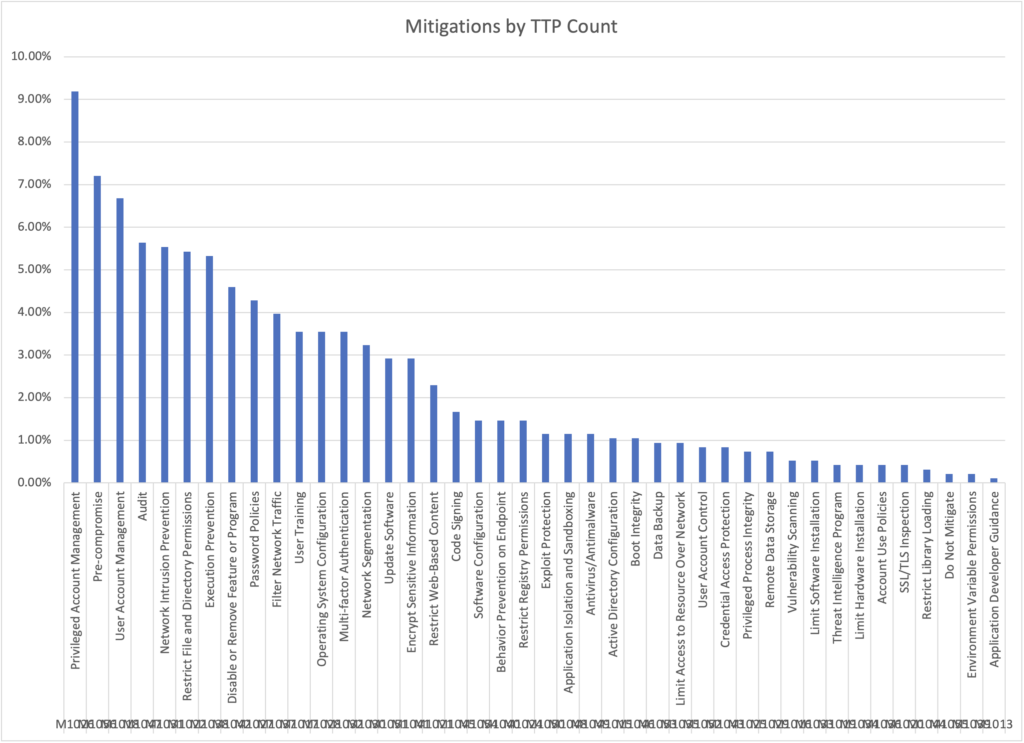
The high level look, the question was how many mitigations were listed per technique? The top 10 were:
- Privileged Account Management
- Pre-compromise
- User Account Management
- Audit
- Network Intrusion Prevention
- Restrict File and Directory Permissions
- Execution Prevention
- Disable or Remove Feature or Program
- Password Policies
- Filter Network Traffic
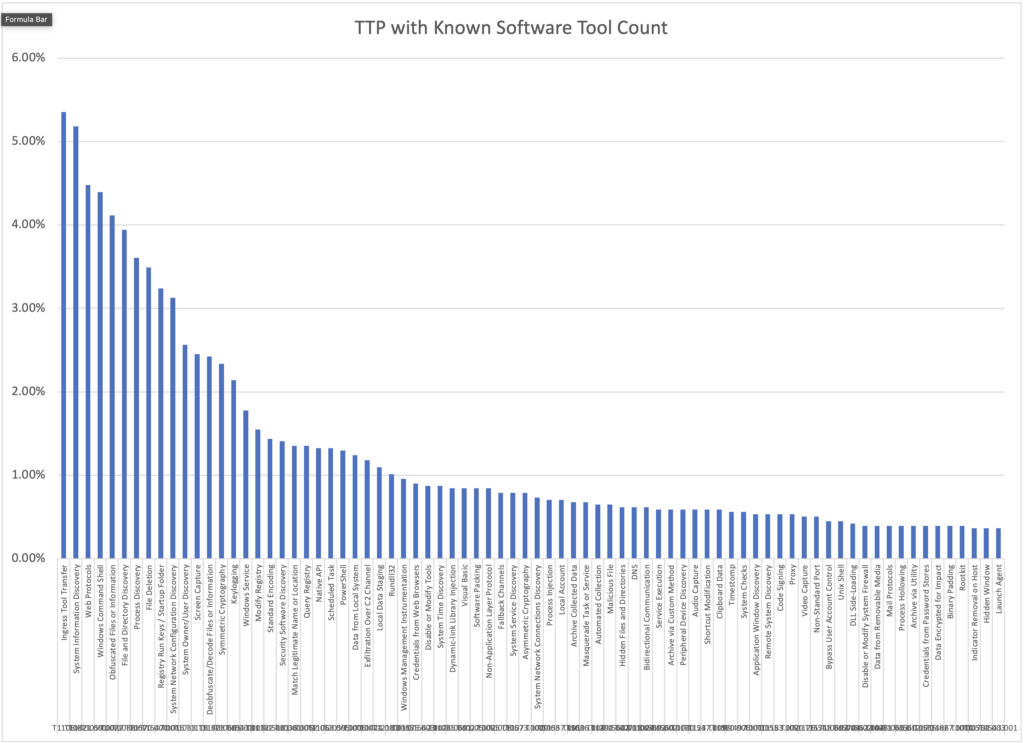
So this caused a question in my mind. What are the most prominent types of techniques out there. The top 10 were:
- Ingress Tool Transfer
- System Information Discovery
- Web Protocols
- Windows Command Shell
- Obfuscated Files or Information
- File and Directory Discovery
- Process Discovery
- File Deletion
- Registry Run Keys / Startup Folder
- System Network Configuration Discovery
So these are easy descriptive statistics. But where this became useful for me is when I started looking at my defenses. My question to my own team and the one that I think you should start with when talking with your team is, “can we detect and deter these types of attacks, and how?”
In my case, the customer I was working with had some manual abilities to do this, but had experienced fairly systemic attacks on some of these fronts. This lead me to two different discussions.
- Are we doing enough to deter / prevent these types of attacks?
- Are we automating our response to these attacks sufficiently?
This lead the team to a more fundamental understanding that before we augment our tool selection we needed to focus on some basics.
As a practitioner, how many times have we focused on tools that promise quick hits in securing our environment when we leave the front door open?
What are the fundamentals for your environment that make your risk mitigation strategy pragmatic, effective and efficient without compromising your user functionality?
For those wanting to look at the analysis, I cannot suggest highly enough the MITRE ATT&CK GitHub page as it has the most recent data on it. But if you want a quick look at my analysis, here is the excel file.