As Chief Information Security Officers, we are often asked to resolve this question. After all, the CISO is responsible for the policies and capabilities of the cyber defense of the organization. But as organizations grow into their Cyber Security awareness, it is often the case that the individual lines of business begin to recognize that it is their bottom line that is impacted – both by good and bad security.
In some organizations we see this playing out as individual lines of business create their own BISO reporting to the CISO, CIO, CTO, or other executive leadership. The question here isn’t so much the specific strategy your organization has adopted, but more to the point, what does owning this risk look like.
To further this conversation, I would ask for a data point to help bring this into focus. Who is involved in your Incident Response Planning? From the position of the CISO, it is clear that there is a technical element to an incident. Let’s call this the Technical Incident Response Plan or TIRP.
But from an executive presence, what is the business role in responding to an incident? Does your leadership know their responsibilities when incidents occur? Do they understand the risk that they are carrying within the line of business – how about the interdependencies? I’ve started to refer to this as the Executive Incident Response Plan or EIRP and how it plays out within your organization is critically important to managing your losses from risks realized.
If you’ve worked on traditional Incident Response Plans, then you’re probably already familiar with the NIST Risk Management Framework. It provides the basic response cycle for handling incidents. While it doesn’t provide insights into specific kinds of threats, it does a great job talking about the programmatic ways in which technical teams go after incidents as they’re happening and a strong reminder to do after-action reviews. But, how does this apply to the executive team? What decisions are they being asked to make during the incident? How is the team communicating with them?
A Quick War Story
A quick aside here and a nod to all of the incident commanders out there. I’m generally not one for war stories, but this example will help illustrate the point. I’ve run quite a few incidents in my time, but every time the incident war room grows there is an asymptotic expansion of the risk. In a recent incident, there was a potential for ransomware because of some threatening emails that had been received. It was quite obvious to us within the company that this was either really weird timing or there was some inside knowledge being leveraged. At any rate, because of the timeliness of the activities, some executives wanted to ‘observe’ the war room to get a better sense of the up-to-the-minute status.
Their presence had two immediate impacts. The first was that they wanted to ‘help’. This took the form of them going into the organization and making decisions to disconnect devices and call external entities – which added to the number of people now in the war room. The second effect was the Incident Response Team was now no longer offering their input in an unfiltered manner. Specifically, it became political because there was an executive presence and no one wanted to appear to be responsible or incorrect in their responses. The cumulative effect was to prolong and exaggerate the response, which ultimately resulted in increased losses from an actual event. In the end, the executive triggered a count down to information being disclosed or deleted because they started ‘investigating’ on their own.
The truth of this is that a good Incident Commander has some very specific qualities that should be imbued upon them during and only during an incident.
- The Incident Commander is the only ‘commander’ in the room. People have different roles and distributed command can be useful, but all command decisions come from one place.
- There is a specific set of decisions and information that is needed by both the Technical and Executive teams. The Incident Commander must decide how to communicate with both teams independently. While this can be delegated, it cannot be collapsed by bringing together the functions.
So What Do I Do?
To help bring this into focus, Cyber Foundry is developing an Incident Response Plan for Executives, Technical Teams, and Incident Commanders. Here is a sample of the new EIRP/TIRP overlay that shows the two very different cycles.
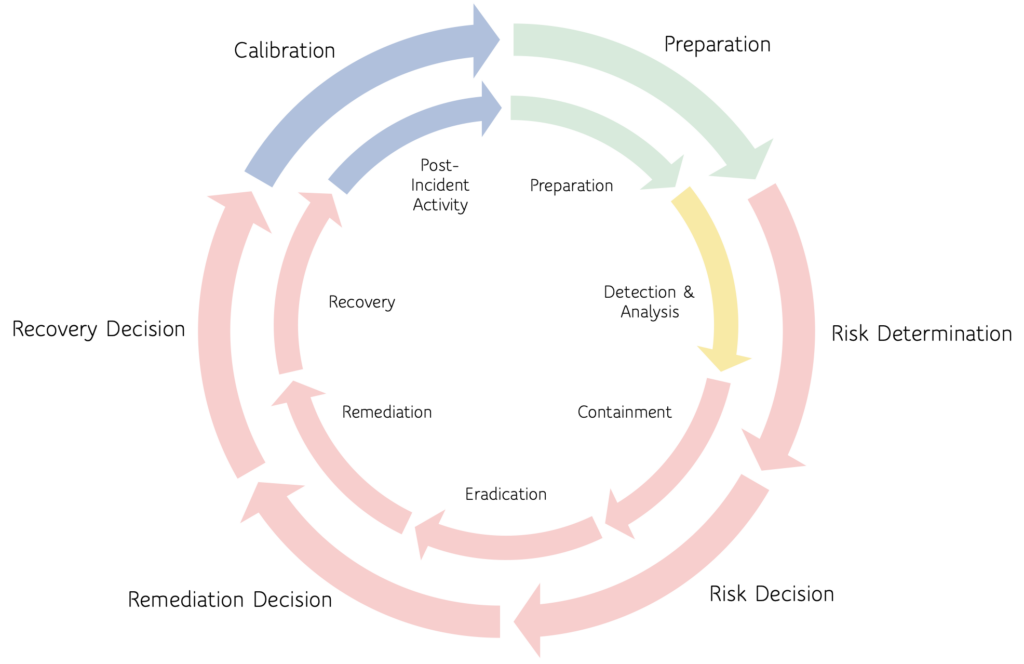
The purpose of this diagram is to show the two overlapping processes. On the inside is the traditional NIST-style Incident Response Plan. However, it is constrained to the Technical side of things so we’ll call it the Technical Incident Response Plan (TIRP). On the outside is the business or executive response cycle which follows the TIRP. We’ll call that the Executive Incident Response Plan (EIRP). Together, these two processes help the Incident Commander respond to the technical and business needs of the organization.
Cyber Foundry will be creating a Risk Management Workshop (riskmanagement.io) which will help train executive and technical teams on this process. But, the idea is here. So I challenge you to think about this problem from the perspective of the business and ask two fundamental questions.
- How does the business respond during a Cyber Security incident to manage decisions that need to be made?
- How effective is your Incident Response Planning when thinking about Crisis Management, Communication, and Compliance Obligations?
If these questions resonate with you and you’re looking for help managing your plan, let’s chat.
About the Author
Bill Weber is the founder of Crypto Foundry, a Cyber Security and DeFi consultancy located in the Washington DC market. With over 30 years in Cyber Security, Crypto Economics, and Information Technology, Bill has worked with organizations like MIT’s Lincoln Laboratory, New York University, Hewlett-Packard, and Microsoft.
CyberFoundry is a consulting company based in Providence Rhode Island. With experience in Government, FinTech, Crypto, DeFi, Healthcare, and Academic industries, our focus is on helping organizations reduce the disruptive forces of Cyber Security threats.